A brand new rip-off known as ClickFix is focusing on customers and rising within the U.S. Because the title suggests, it asks you to click on on a hyperlink, claims to repair a problem, however truly In it infects your laptop with malware.
I This was reported earlierDetailing how menace actors used bugs that mimic messages from Google Chrome, Microsoft Phrase and OneDrive to contaminate customers’ computer systems.
Now the same assault is having an impact Google Meet Customers, whether or not they’re utilizing Home windows PC or Mac. I clarify how this cyber assault works and what you are able to do to guard your self.
I’m giving away a $500 gift card for the holidays
A lady works on her laptop computer (Kurt “Cyberguy” Knutson)
How Google Meet Entice works
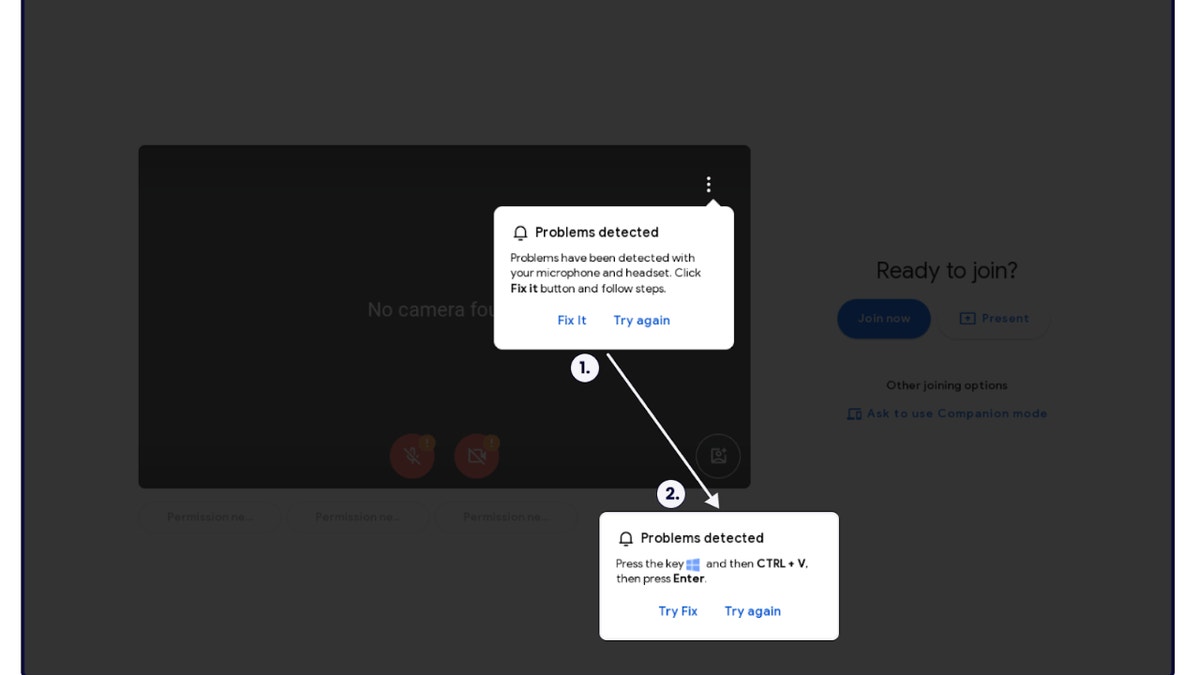
In line with the French Cyber security company SequoiaAll of it begins with an e-mail with a hyperlink to a Google Meet. E-mail can come from any handle and will be socially engineered to seem to belong to your group. This is usually a hyperlink to a Google Meet invitation to a gathering, webinar, on-line collaboration, or one thing comparable. If you click on on the hyperlink, you’ll be redirected to a faux Google Meet web page, which is able to quickly show a warning claiming that there’s a downside together with your PC. This will likely imply that your microphone or digital camera isn’t working or that there’s a downside together with your headset.
What is Artificial Intelligence (AI)?
You’ll be able to count on to see the next URLs in these faux assembly emails:
be part of(.)google(.)us-join(.)com
be part of(.)google(.)web-join(.)com
Meet(.)googie(.)com-join(.)us
meet(.)google(.)cdm-join(.)us
This faux web page will even show a pop-up providing to repair the issue, exhibiting phrases like “key mixture” or “CTRL+V”. If you observe these directions, the malicious code is pasted in Windows promptInfecting your laptop with malware. As soon as the code is in your laptop, hackers can acquire entry to your cryptocurrency, delicate information and private data.
Sequoia has uncovered a number of different malware distribution clusters past Google Meet. These embrace platforms similar to Zoom, PDF readers, faux video video games (similar to Lunacy, Calypso, Battleforge and Regan), tasks similar to Web3 Browser and NGT Studio, and messenger apps similar to Nortex.
Pretend Google Meet web page (sequoia)
Don’t let your voicemail get bogged down with this quick tip
massive image
Again in July, McAfee seen that ClickFix campaigns had been on the rise, particularly within the US and Japan (by way of Bleeping computer). Just lately, two teams – Slavic Nation Empire and ScamQuarteo – have been behind a few of these assaults. Each are mentioned to be branches of main crypto rip-off gangs Marco Polo and Crypto Love.
Earlier this yr, Proofpoint discovered that The malware was spreading by pretending to be fake error messages For Google Chrome, Phrase and OneDrive, tricking folks into downloading malicious code. Additionally they pointed to a way known as “e-mail luring”, the place hackers ship faux emails pretending to be from MS Phrase to contaminate computer systems.
Get FOX Business on the go by clicking here
Pretend web page requests (sequoia)
Best Antivirus for PCs, Macs, iPhones and Androids – Cyberguy Picks
4 methods to guard your self from dangerous software program
A faux Google Meet web page creates a way of urgency, inflicting customers to click on on hyperlinks and unwittingly compromise their units. There are a number of steps you may take Protect yourself from such cyber attacks.
1. Have sturdy antivirus software program: One of the best ways to guard your self from clicking on malicious hyperlinks that set up malware that features entry to your private data is to put in antivirus safety on all of your units. It could actually additionally provide you with a warning to any phishing emails or ransomware scams. Get my picks for 2024’s best antivirus security winners for your Windows, Mac, Android, and iOS devices.
2. Monitor your accounts: Often assessment your financial institution statements, bank card statements and different monetary accounts for any unauthorized exercise. In case you see any suspicious transactions, report them to your financial institution or bank card firm instantly.
3. Alert fraud: Contact one of many three main credit score reporting companies (Equifax, Experian or TransUnion) and request a fraud alert be positioned in your credit score file. This can make it harder for id thieves to open new accounts in your title with out verification.
4. Allow two-factor authentication: allow Two-factor authentication Every time potential. It provides an additional layer of safety by requiring a second type of verification, like a code despatched to your cellphone, along with your password.
How to remove your personal data from the Internet
Kurt’s major measures
Hackers have tricked you into putting in malware. They use social engineering to make emails and web site prompts look professional, hoping you will click on the hyperlink and observe their directions. One of the best ways to guard your self is to keep away from unknown hyperlinks and all the time examine the URL of the web page you might be on earlier than taking any motion.
Click here to get the Fox News app
Have you ever ever obtained an e-mail or immediate that appeared suspicious however appeared professional at first look? Inform us by writing to us Cyberguy.com/Contact.
For extra of my tech suggestions and safety alerts, subscribe to my free Cyberguy Report e-newsletter by visiting Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you want covered.
Comply with Kurt on his social channels:
Solutions to probably the most continuously requested CyberGuy questions:
New from Kurt:
Copyright 2024 CyberGuy.com. all rights reserved.

