A brand new malware suspected of spying has been found by safety researchers. Hackers infect gadgets by impersonating authorities businesses, often tax businesses such because the Inside Income Service (IRS). As soon as the malicious software program is on the PC, it may possibly collect intelligence (accumulate private knowledge, passwords and extra), obtain extra malicious software program and add knowledge to the hacker’s server. It does all this whereas utilizing Google Sheets to keep away from suspicion and retailer knowledge.
Get security alerts, expert tips – sign up for Kurt’s newsletter – CyberGi Report here
Instance of a pc being hacked by malware (Kurt “Cyberguy” Knutson)
All of it begins with a pretend e mail
The hackers behind the malware, dubbed “Voldemort,” have cleverly crafted it to keep away from being caught. Because the title Voldemort in JK Rowling’s Harry Potter sequence spells out the issue, it is inflicting issues within the cybersecurity world as nicely.
A cyber assault begins once you obtain an e mail that seems to be from a authorities tax company. Accordingly Proof pointHackers behind this marketing campaign are impersonating tax businesses in varied international locations together with the US (IRS), UK (HM Income & Customs), France (Path Générale des Funds Publiques), Germany (Bundeszentralamt für Steuern), Italy (Agenzia). are delle entrete) and, by 19 August, India (Revenue Tax Division) and Japan (Nationwide Tax Company). Every e mail lure was personalized and written within the language of the tax authority.
Proofpoint analysts discovered that hackers tailor-made their phishing emails to match the goal’s nation of residence primarily based on publicly accessible data relatively than the situation of the group or the language steered by the e-mail deal with. For instance, some targets in a European group obtained emails impersonating the IRS as a result of they had been linked to the US in public data. In some circumstances, hackers matched the nation of residence when the goal shared a reputation with one other outstanding particular person.
The e-mail additionally tries to impersonate authorities company e mail. For instance, pretend emails had been despatched to individuals within the US utilizing “no_reply_irs(.)gov@amecaindustrial(.)com”.
E mail that tries to impersonate a authorities company e mail (Proofpoint) (Kurt “Cyberguy” Knutson)
The assault cleverly seems in your machine
Within the pretend e mail, hackers impersonating the federal government warn you about modifications to tax charges and tax programs and ask you to click on a hyperlink to learn an in depth information. Clicking the hyperlink brings you to a touchdown web page, which makes use of the Google AMP cache URL to redirect you to a web page with a “Click on to view doc” button.
After clicking the button, hackers test in case you are utilizing a Home windows machine. In case you are, you may be redirected to a different web page. If you work together with that web page, it triggers a obtain that appears like a PDF file in your PC’s Downloads folder, however is definitely an LNK or ZIP file hosted on an exterior server.
If you open the file, it runs a Python script from one other server with out truly downloading the script to your laptop. This script collects system data to profile you, whereas opening a pretend PDF to cover errant exercise.
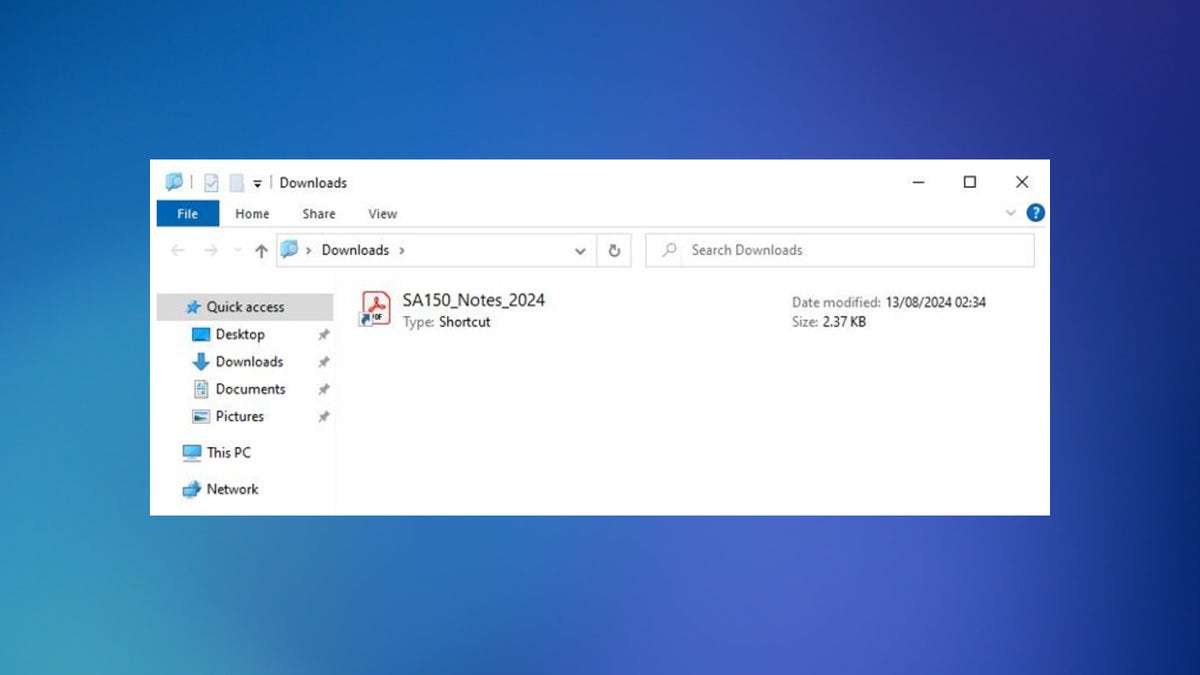
Obtain what seems to be like a PDF file to your PC’s Downloads folder (Proofpoint). (Kurt “Cyberguy” Knutson)
Voldemort makes use of Google Sheets to retailer knowledge
As soon as the malware has efficiently contaminated your Home windows machine, it may possibly:
- ping: Verify whether it is nonetheless related to its management server
- Dir: Get a listing of information and folders in your system
- Obtain: Ship information out of your system to the management server
- Add: Put the information from the management server onto your system
- govt: Run particular instructions or applications in your system
- Copy: Copy information or folders to your system
- transfer: Transfer information or folders in your system
- sleep: Cease its exercise for a specified time
- exit: Cease operating in your system
The malware makes use of Google Sheets as its command heart, the place it receives new directions and shops stolen knowledge. Every contaminated machine sends its knowledge to particular cells within the Google sheet, marked by distinctive IDs to maintain the whole lot organized.
Voldemort interacts with Google Sheets by way of Google’s API, utilizing an embedded shopper ID, secret and refresh token saved in its encrypted settings. This methodology offers malware a dependable strategy to talk with out elevating suspicion as a result of Google Sheets is broadly utilized in companies, making it troublesome for safety instruments to dam it.
How to recognize and avoid falling victim to vacation rental scams
4 Methods to Defend Your self from Malware Assaults
Hackers are releasing an increasing number of refined malware, however that does not imply you are helpless. Beneath are some ideas to assist shield your self from such assaults.
1) Learn delicate emails fastidiously: One of the simplest ways to identify pretend emails that ship malware is to fastidiously study them. Whereas hackers could also be tech-savvy, their language abilities are sometimes not excellent. For instance, within the screenshots above, you might even see errors like “taxplayer” as an alternative of “taxpair”. Authorities businesses do not often make these sorts of errors.
2) Verify the e-mail area: Confirm that the e-mail area matches the group it claims to characterize. For instance, an e mail from the IRS should come from an deal with ending in “@irs.gov.” Watch out for minor misspellings or variations within the area.
3) Put money into knowledge elimination providers: Hackers goal you primarily based in your publicly accessible data. This might be something out of your leaked data to data you supplied to an e-commerce store by way of an information breach. Check out my top picks for data removal services here.
4) Have sturdy antivirus software program: In case you have sturdy antivirus software program put in in your machine, it may possibly shield you once you obtain most of these rip-off emails or by accident open an attachment or click on on a hyperlink. One of the simplest ways to guard your self from clicking on malicious hyperlinks that set up malware that beneficial properties entry to your private data is to put in antivirus safety on all of your gadgets. It could actually additionally provide you with a warning to any phishing emails or ransomware scams. Get my picks for 2024’s best antivirus security winners for your Windows, Mac, Android, and iOS devices.
Subscribe to KURT’s YouTube Channel for quick video tips on how to work all your tech devices
Kurt’s key takeaway
Though researchers cannot say for certain, most of the methods utilized by the malware are just like these employed by hackers suspected of espionage. Even when this evaluation seems to be flawed, the dimensions and class of the assault is regarding. Anybody with out technical data can simply turn out to be a sufferer and lose private knowledge and cash. The assault particularly targets Home windows customers, which additionally raises questions on Microsoft’s safety framework.
What measures do you suppose organizations ought to implement to higher shield people from malware assaults? Inform us by writing to us Cyberguy.com/Contact.
For extra of my tech ideas and safety alerts, subscribe to my free Cyberguy Report publication by visiting Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you want covered.
Comply with Kurt on his social channels:
Solutions to probably the most often requested CyberGuy questions:
New from Kurt:
Copyright 2024 CyberGuy.com. all rights reserved.

