Have you ever ever had that sinking feeling that one thing’s not fairly proper together with your laptop? Possibly it’s working slower than typical or there are new icons in your desktop that you just don’t acknowledge. Nicely, you won’t be simply imagining issues; you would have been hacked.
Whereas the primary response could also be to panic, the very best first step in the event you assume you’ve been hacked is to disconnect your laptop from the web and take a deep breath. When you’ve received antivirus software program already put in, run the scan instantly. However don’t fear simply but. Earlier than you begin fretting about cyberthieves and misplaced information, let’s take a second to stroll by some essential steps collectively. From working a trusty antivirus scan to the nitty-gritty of browser settings and distant entry – that is your go-to information for outsmarting these pesky hackers.
GET SECURITY ALERTS, EXPERT TIPS – SIGN UP FOR KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
A lady grabbing her laptop in frustration (Kurt “CyberGuy” Knutsson)
Had been you hacked?
1. Run antivirus software program ASAP
While you’re working any antivirus scans or troubleshooting, begin from the precise antivirus software program program. Don’t comply with pop-ups or notifications. If there may be certainly a compromise, it ought to present up on the dashboard of the antivirus software program program.
Preventative:
- Hold your antivirus software up to date. Hackers are developing with new viruses usually, so in case you are updated, you’re much less more likely to be compromised. Or the virus is extra more likely to get caught.
- Be conversant in your antivirus software program notifications and alerts, so in the event you ever get a pop-up or notification, you’ll be extra apt to note faux ones.
- Write down the contact data of the antivirus software program you’ve got put in and have it close to the pc.
When you really feel fairly assured that you just’ve sadly been hacked, however your antivirus scan comes up empty, take a break and name customer support of antivirus software program immediately. Don’t comply with hyperlinks to have a rep name you. Use the quantity you’ve got written down, and name them immediately so you recognize you are not being duped.
When you don’t have antivirus software program put in, be sure that to put in one and do a pc scan. Yow will discover our high suggestions here.
ASK ANY TECH QUESTION AND GET KURT’S FREE CYBERGUY REPORT NEWSLETTER HERE
A person typing on keyboard (Kurt “CyberGuy” Knutsson)
HOW TO RECOVER A HACKED FACEBOOK ACCOUNT
2. Reformat or reset to manufacturing facility settings
Typically a virus or different nefarious entities have overrun the pc so badly that you just would possibly want to easily reformat or reset it to manufacturing facility settings. When you’ve uninstalled or deleted suspicious packages or functions solely to have them reload upon restarting your laptop, it’s possible you’ll merely want to start out from scratch. Because of this it’s essential to have latest backups of your information. Our article, “How to securely get rid of your old PC or Mac,” outlines easy methods to reset to manufacturing facility settings or reformat your laptop.
EXPERT TIPS, LEGIT REVIEWS. GET THE FREE CYBERGUY REPORT NEWSLETTER
3. Delete settings or extensions on browsers or uninstall and reinstall browsers fully
There have been many occasions I’ve gone to assist my mother along with her on-line accounts, solely to be inundated with pop-ups, redirects or random hyperlinks on her browser bar or menu. It turned out that she had both by chance downloaded extensions that embedded themselves within the browser or, worse, modified the browser setting to open a spammy web site as her foremost search engine or touchdown web page. You may go to settings or preferences and delete extensions you don’t acknowledge. But when these settings or extensions maintain reappearing after deleting and restarting the browser, it’s seemingly an even bigger drawback. Then, uninstall the browser and see in the event you can reinstall it. If that brings up the identical settings once more, then it might be a way more invasive virus or malware that must be addressed with an antivirus scan or help from an expert.
HOW TO OUTSMART CRIMINAL HACKERS BY LOCKING THEM OUT OF YOUR DIGITAL ACCOUNTS
4. Flip off or prohibit distant entry
Whereas it’s tougher for hackers to entry your laptop whether it is fully turned off, you probably have allowed distant entry, a hacker simply wants your laptop to be hooked as much as a community or the web with the intention to take over your system and switch it on.
To forestall distant entry to your PC:
- Click on the Home windows Begin button
- Enter Distant Desktop settings within the search bar
- Within the Distant Desktop settings, be certain that the slider underneath “Allow Distant Desktop” is ready to Off.
- Evaluate your present processes in Process Supervisor (Ctrl+Alt+Del) for any uncommon or suspicious actions
To forestall distant entry on Macs:
- Click on the Apple brand icon within the high left nook.
- Click on System Settings
- Faucet Normal
- Click on the Sharing icon
- Scroll down and uncheck the packing containers subsequent to Distant Login and Distant Administration to forestall unauthorized distant entry.

A lady on her laptop computer (Kurt “CyberGuy” Knutsson)
HOW HACKERS CAN CRAFT AN ATTACK FROM YOUR SOCIAL MEDIA PROFILE
5. Evaluate your exercise monitor in your laptop and community visitors patterns
Periodically, checking your laptop’s exercise monitor to test which packages are working and what’s utilizing up probably the most bandwidth is a wholesome apply. It would train you to identify any packages or visitors that’s uncommon or if another person is connecting to your laptop remotely.
To evaluate this exercise in your PC:
- Go to Management Panel
- Click on Administrative Instruments
- In Occasion viewer, search for the occasions which are associated to startup and shutdown. Any shutdown can be listed there and which program or user-initiated that startup or shutdown. This fashion, you may see if these actions are that of a virus or an replace course of.
To evaluate this exercise in your Mac:
- Go to the menu bar on the highest left if you first go online to your account.
- Choose Go
- Within the drop-down menu, choose Utilities
- When a menu pops up, one of many first choices must be Exercise Monitor.
Or:
- Go to your Purposes folder in your dock (often positioned on the underside or right-hand aspect of the display screen)
- Go to Utilities folder
- Choose Exercise Monitor

A person placing in his username and password on pill (Kurt “CyberGuy” Knutsson)
Prime 3 preventative measures to not get hacked
1. Activate 2-factor authentication
Whereas it could seem to be a ache to enter a code obtained through e mail or textual content every time you check in, this additional step is essential for safety. By activating two-factor authentication, you create a barrier in opposition to unauthorized entry. Even when a hacker discovers your e mail or username, they received’t get far with out the distinctive code.
Every login try triggers a notification, alerting you to potential threats. Repeated failed makes an attempt will safe your account by both locking it or sending you an alert. Within the occasion of suspicious exercise, you may swiftly use a trusted system to reset your password and inform the service supplier. It’s a small value to pay for important safety in opposition to cyberthreats.

A person backing up his laptop (Kurt “CyberGuy” Knutsson)
2. Have sturdy antivirus software program
The easiest way to guard your self from clicking malicious hyperlinks that set up malware in an try and get entry to your personal data is to have antivirus safety put in on all of your units. This may additionally warn you of any phishing emails or ransomware scams. Plus, consider it like having a digital bodyguard – all the time looking out, all the time able to defend you from cyberthreats. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
3. Configure your e mail settings
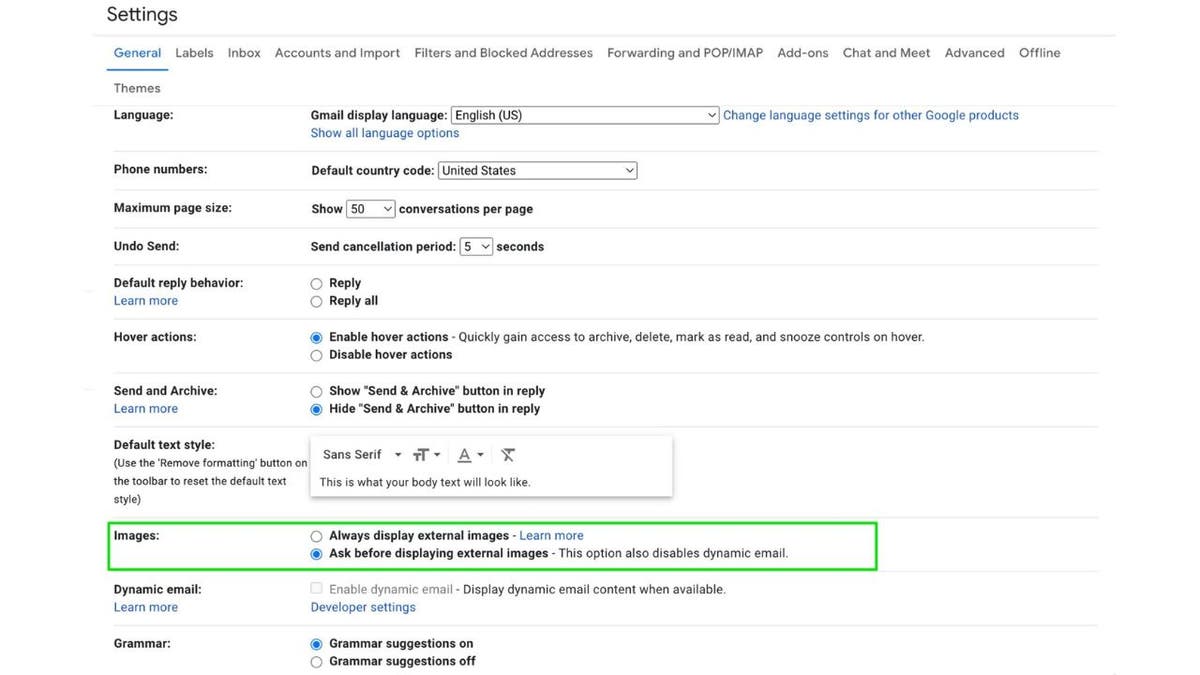
Configure e mail settings to not robotically pictures or attachments (Kurt “CyberGuy” Knutsson)
When you configure your e mail settings to not robotically load content material equivalent to pictures or attachments, then it’s tougher for viruses or different malware to be robotically downloaded or by chance opened. When you even have emails obtained first in wealthy textual content format, you may select which emails load absolutely with pictures when you understand it’s from a trusted supply.
Gmail desktop:
- Click on the settings gear icon
- Select See all settings
- Underneath the Normal tab, scroll to the Photos part.
- Choose Ask earlier than displaying exterior pictures
- Scroll to the underside of the web page and click on Save Modifications
Gmail cellular:
- Faucet the hamburger menu (3 horizontal traces)
- Choose Settings
- Select the account you wish to handle
- Scroll to the Photos part and choose Ask earlier than displaying exterior pictures.
Apple mail:
- First, click on on Mail in your dock on the backside of your display screen
- Then click on on Mail within the higher left of your display screen
- Click on Settings
- Go to the Viewing tab
- Uncheck Load distant content material in messages
Outlook desktop (PC):
- Click on File
- Select Choices
- Choose Belief Middle
- Click on Belief Middle Settings
- Underneath Computerized Obtain, test the choice that claims Don’t obtain footage robotically in commonplace HTML e mail messages or RSS gadgets.
Outlook desktop (Mac):
- Open Outlook
- Click on Preferences
- Underneath Electronic mail choose Studying
- Select Safety
- Choose By no means to forestall picture downloads
Yahoo Mail desktop:
- Click on Settings.
- Select Extra Settings.
- Click on Viewing e mail.
- Underneath Present pictures in messages, choose Ask earlier than exhibiting exterior pictures.
Begin Mail desktop:
Please word that the precise wording of the menu gadgets and choices can differ primarily based on the model of Begin Mail you’re utilizing.
- Open Begin Mail
- Click on on the Settings icon
- Navigate to the Electronic mail section
- Search for the Photos or Privateness settings
- Select the choice to Ask earlier than displaying exterior pictures or an analogous setting that controls the automated downloading of images.
These steps ought to assist improve your e mail safety by providing you with management over which pictures are displayed, thereby lowering the chance of malware being robotically downloaded or opened. At all times guarantee your e mail utility is up to date to the most recent model for the very best safety practices.
On the lookout for personal and safe e mail options? See Best Private and Secure Email Providers 2024
QUICK TIPS. EXPERT INSIGHTS. CLICK TO GET THE FREE CYBERGUY REPORT NEWSLETTER
Knowledge restoration: Defending your data in opposition to loss
This may increasingly not appear related to an article about hacking, however having your information off your laptop and safely on an exterior onerous drive or the cloud offers you extra choices in the event you assume you’ve been hacked. When you need assistance deciding what sort of knowledge backup can be finest for you, please check out these articles:
If a hack is unhealthy sufficient, generally a whole wipe of your system is the one option to salvage your laptop. When you’ve got a secure copy of your information, whereas it is likely to be inconvenient, you’ll not lose all of your information. Additionally, in the event you maintain extra delicate information off your extra often used laptop, then your information is much less more likely to be compromised in the event you get hacked.
Kurt’s key takeaways
On the finish of the day, being hacked is an enormous inconvenience and might doubtlessly result in information loss or theft. However do not lose hope. There are steps you may take to outsmart these pesky hackers and maintain your units safe. The bottom line is staying vigilant and taking preventative measures like utilizing sturdy antivirus software program, enabling two-factor authentication and repeatedly backing up your information. That method, in the event you do get hacked, you may have a latest backup to depend on and might merely wipe your system clear with out dropping all the pieces.
It is also essential to maintain a watch out for any suspicious exercise in your laptop or community. If one thing appears off, do not hesitate to run a full antivirus scan and evaluate your exercise monitor for any unauthorized entry or packages working within the background. Bear in mind, hackers are all the time developing with new methods, so it is an ongoing battle to remain one step forward. However by following the guidelines outlined right here, you may be properly in your option to conserving your digital life safe and hack-free. Keep vigilant, my associates.
Are you able to share a private story the place being proactive about laptop safety paid off or, conversely, the place neglecting it led to points? Tell us by writing us at Cyberguy.com/Contact.
For extra of my tech suggestions and safety alerts, subscribe to my free CyberGuy Report E-newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Observe Kurt on Facebook, YouTube and Instagram.
Solutions to probably the most requested CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.

