‘Cybergai’: Spring’s backup
Defending your digital life with dependable bodily backups is not only a precaution, it is a necessity. Kurt Knutsson offers the important backup guidelines.
Chances are high, you are lots nearer to a web-based safety catastrophe than you suppose. Details about you is unfold far and vast on-line, and dropping management of this digital id might be embarrassing at greatest and financially devastating or personally harmful.
Whereas it might appear overwhelming at first, we’re right here that can assist you keep protected on-line. We have compiled a listing of all of the steps you possibly can take to remain protected on-line. As a result of there may be numerous info, we advise you’re employed by way of it at your personal tempo.
Get security alerts, expert tips – sign up for Kurt’s newsletter – CyberGi Report here
A lady harassed about a web-based catastrophe (Kurt “Cyberguy” Knutson)
Step 1 – Allow computerized updates
Preserve your software program of up to the date is without doubt one of the best methods to maintain your self protected on-line. Whether or not you might be utilizing a Home windows machine, a Mac, an iPhone or an Android smartphone, all these gadgets are usually up to date with new safety fixes. It is a good suggestion to double verify and ensure your system’s computerized updates are turned on. as follows:
Home windows 10 computerized replace
From the Begin menu, go to Settings > Replace & Safety > Home windows Replace. From the Home windows Replace part, you will see a variety of choices for updating Home windows. Right here you possibly can arrange your “lively hours” to make sure that Home windows mechanically reboots and installs updates outdoors of your waking or working hours.
Home windows 11 computerized replace
Home windows 11 customers will click on on the Home windows icon and proceed Settings > Home windows Replace > Superior choices. From right here, you possibly can management when Home windows Replace will run, much like the “Lively Hours” management in Home windows 10.
macOS
Mac customers can open Click on System Preferences > Software program Replace and the “Superior” button. Within the “Superior” part, ensure that every field is checked, as this can be certain that they obtain Well timed OS updates.
iOS
If you wish to activate computerized updates with iPhone, open Settings > Basic > Software program Replace And ensure that Computerized replace is on
android
In case you have an Android system, open Settings > System > Superior > System Replace And ensure System replace The setting is on on the
Auto parts giant exposed: 2.3 customers at risk of big data breach
Step 2 – Use a robust password
Reusing the identical password throughout a number of web sites or purposes is without doubt one of the commonest cybersecurity errors. For those who use the identical password for a couple of factor, it solely breaches one service to reveal your different accounts. Utilizing a password the manager A straightforward resolution is to create robust passwords for a number of accounts.
Instance of defending your system (Kurt “Cyberguy” Knutson)
The world’s largest stolen password database uploaded to the Criminal Forum
Step 3 – Arrange and use two-factor authentication
Two-factor Authenticity It is an effective way so as to add an additional layer of safety to your on-line accounts. Enabling two-factor authentication makes it more durable for hackers to entry your account, as your account would require a one-time code along with a password to log in.
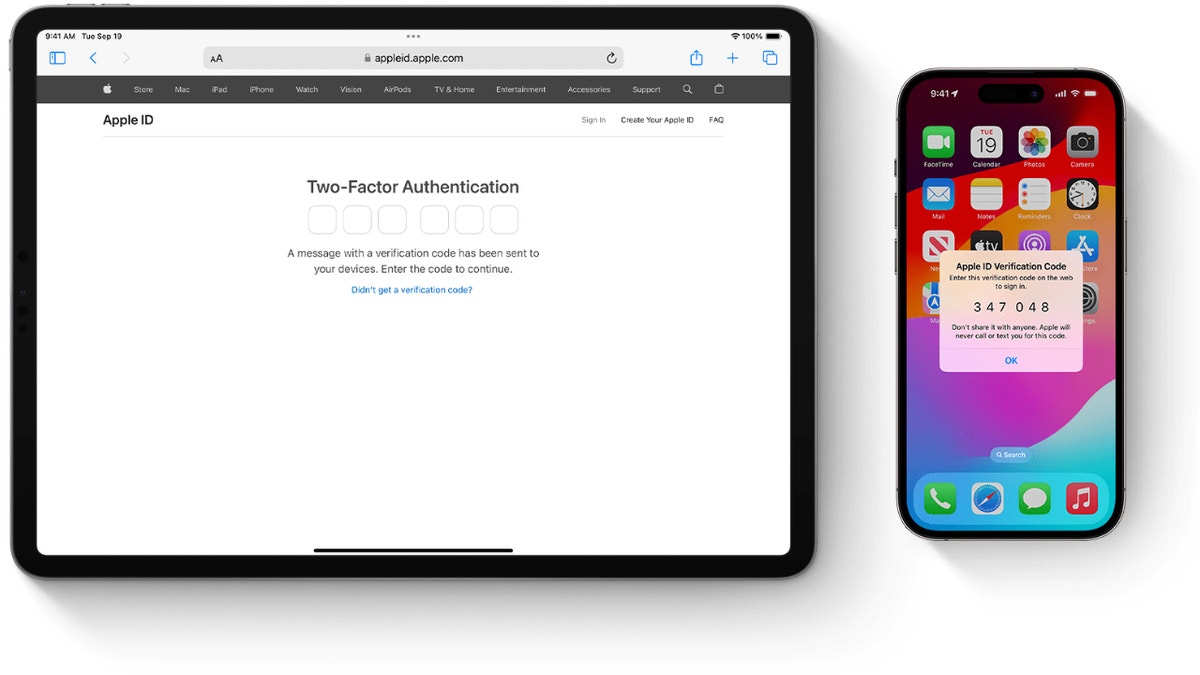
Two-factor authentication is being featured on Apple gadgets (Apple). (Kurt “Cyberguy” Knutson)
Step 4 – Encrypt your pc’s storage
For those who lose your laptop computer, pill or cellphone, all the private info on these gadgets might be accessible to anybody who finds it. A straightforward option to shield your self on this scenario is to encrypt your gadgets beforehand. encryption It makes it onerous for hackers to learn the info, and whereas it sounds sophisticated, the precise course of is straightforward to arrange.

Visualization of information on a pc display screen (Kurt “Cyberguy” Knutson)
Step 5 – Discover or erase the misplaced system
For those who misplaced your system earlier than encrypting it, there isn’t any want to fret an excessive amount of. Discovering a misplaced smartphone or remotely wiping it’s simpler than ever. We’ve got an awesome information on what to do you probably have Lost your phone for both Androids and iPhones.
You may also use the same course of to search out misplaced ones Windows laptop or MacBook. As working techniques have moved to retailer info within the cloud, it is easy to wipe a misplaced laptop computer. For those who lose a laptop computer in public, we suggest wiping it remotely as quickly as potential to make sure your information hasn’t been taken by a malicious actor.
Step 6 – Have robust antivirus software program
One of the simplest ways to guard your self from clicking on malicious hyperlinks that set up malware that positive aspects entry to your private info is to put in antivirus safety on all of your gadgets. It may additionally provide you with a warning to any phishing emails or ransomware scams. Get my picks for 2024’s best antivirus security winners for your Windows, Mac, Android, and iOS devices.
Step 7 – Save your net browser
We use our net browsers every day. Whether or not from a laptop computer, a desktop or a smartphone, you in all probability use your net browser greater than most different apps. Taking a couple of minutes to usually replace your browser to the newest model, being cautious concerning the web sites you go to and avoiding doubtful downloads are all vital practices that complement your browser’s safety features.
By implementing these safety measures, you might be defending your browser, private info, monetary information and total digital id. Exposure to security risk by potential hackers and cybercriminals.
Step 8 – Defend your smartphone
Smartphones now function extensions of our private lives, used for every little thing from banking to scheduling physician appointments. Conserving your smartphone protected is extra vital than ever, and fortuitously, each Android and iOS characteristic a variety of built-in options to assist shield your private info.
To extend your self iPhone or Android’s For safety, begin by enabling a robust lock display screen methodology equivalent to a fancy passcode, fingerprint recognition or facial recognition. Use warning when utilizing Public Wi-Fi networks And think about using a VPN For further safety.

An individual who has an Android cellphone (Kurt “Cyberguy” Knutson)
10 simple steps to improve the security and privacy of your smartphone
Step 9 – Safe your wi-fi community
Your own home Wi-Fi community can energy your good residence gadgets, however it might probably additionally go away you Vulnerable to hackers. Happily, it is easy to enhance yours Home wireless settings To maintain your self extra protected. As with our earlier steps, you will wish to ensure that your router has the latest up to date firmware and that you just use two-factor authentication and a robust password to your wi-fi connection.

Individuals utilizing wi-fi networks on their computer systems (Kurt “Cyberguy” Knutson)
Step 10 – Again up your information usually
Backing up your information usually protects your digital life from {hardware} failure, theft or cyber assaults. Select a dependable backup methodology that fits your wants, eg the cloud storage or External hard drive. Arrange computerized backups to run repeatedly, overlaying all of your gadgets, together with smartphones and tablets. Defend your backups through the use of robust passwords, enabling two-factor authentication for cloud storage or encrypting bodily backups.
Periodically, take a look at your backups by restoring information to ensure the system works correctly. Bear in mind, a stable backup technique is an important a part of your total cybersecurity plan, offering safety and peace of thoughts.
Step 11 – Put money into private information removing companies
In as we speak’s digital panorama, your private info can find yourself in lots of on-line databases and folks search websites with out your data or consent. These information aggregators gather and promote your info, probably exposing you to privateness dangers and unsolicited requests. Utilizing an information removing service may help scale back these dangers by systematically eradicating your private info from these databases.
Whereas no service guarantees to take away your entire information from the Web, a removing service is nice if you wish to repeatedly monitor and automate the method of eradicating your info from a whole bunch of websites over a protracted time frame.
By lowering your digital footprint, you scale back the chance of your private info being misused for id theft, focused promoting or different privacy-invasive practices. Whereas utterly erasing your on-line presence is difficult, utilizing an information removing service is an efficient step towards regaining management over your private info and growing your total on-line privateness and safety. Check out my top picks for data removal services here.
Kurt’s most important measures
Securing your on-line presence could seem daunting, however bear in mind, it is all about taking small, constant steps. Consider it as constructing a digital fortress: every measure you implement is one other brick in your cybersecurity wall. Do not feel pressured to deal with every little thing without delay. Begin with the fundamentals, like enabling computerized updates and utilizing a robust password, then steadily work your means by way of the opposite steps. The digital world is consistently evolving and so should our safety practices.
How has your strategy to on-line safety modified through the years and what impressed these modifications? Inform us by writing to us Cyberguy.com/Contact.
For extra of my tech ideas and safety alerts, subscribe to my free Cyberguy Report publication by visiting Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you want covered.
Observe Kurt on his social channels:
Solutions to essentially the most incessantly requested CyberGuy questions:
Copyright 2024 CyberGuy.com. all rights reserved.

