What is Malware?
Kurt “Cybergai” Knutson discusses easy methods to defend your self from malware and ransomware.
New and complicated malware mimicking Google Chrome and Microsoft have the potential to steal cash from Home windows machine homeowners, on-line safety agency Proofpoint has warned. A number of teams of cybercriminals are utilizing this malware, with some identified to ship spam emails that may infect computer systems. Malware or Ransomware.
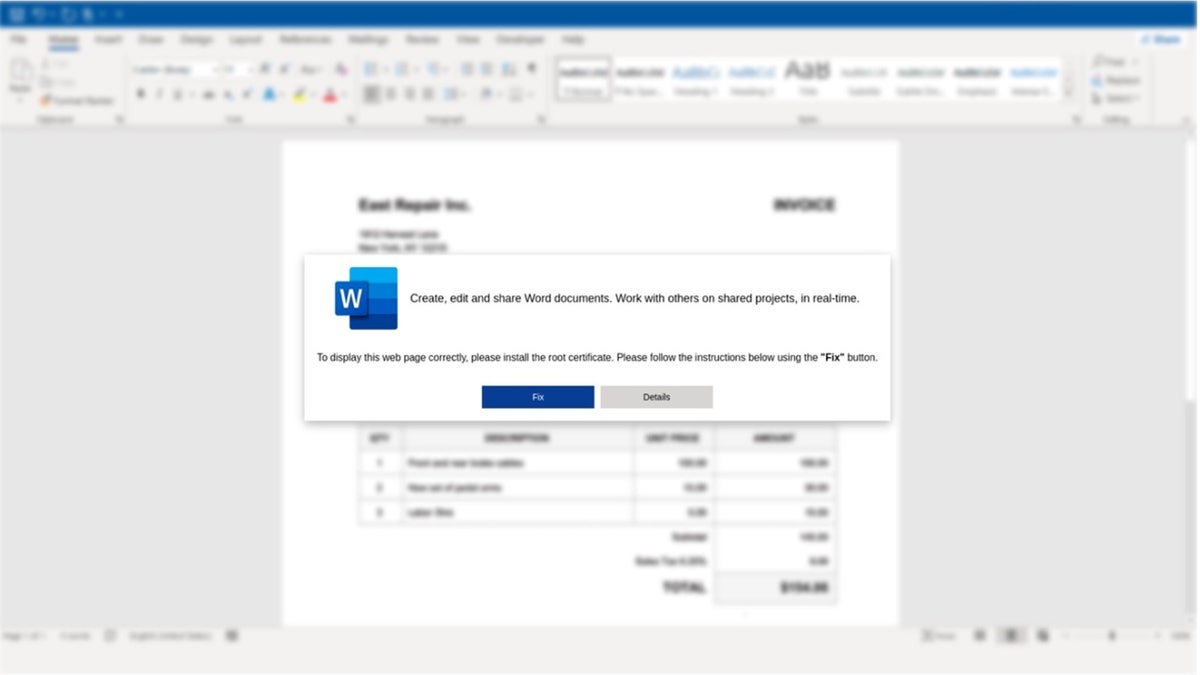
The malware presents itself as faux updates to Web browsers like Chrome to trick customers into downloading malicious code. As soon as the code is on a pc, hackers can entry cryptocurrencies, delicate information and private data.
Get security alerts, expert tips – sign up for Kurt’s newsletter – CyberGi Report here
Microsoft Laptop computer (Microsoft) (Kurt “Cyberguy” Knutson)
How does faux replace malware work?
Proof point recognized a big distribution of malware this month, however the on-line safety agency believes the marketing campaign has been ongoing since March 2024. The malware presents faux Google Chrome, Phrase and OneDrive errors to power customers to obtain dangerous code. These errors immediate the customer to click on a button to repeat the PowerShell “repair” to the clipboard, then paste and run it into the Run dialog or PowerShell immediate.
“Though a collection of assaults require important consumer interplay to succeed, social engineering is intelligent sufficient to current somebody with an actual downside and resolution, which might immediate a consumer to take motion with out contemplating the danger. is,” warns Proofpoint.
When the PowerShell script runs, it checks if the machine is a legitimate goal. Then, it downloads extra payloads. These steps embody clearing the DNS cache, eradicating the clipboard contents, displaying a faux message, and downloading one other distant PowerShell script.
ClickFix Error Message (Proofpoint) (Kurt “Cyberguy” Knutson)
Best Antivirus for PCS, MACS, IPHONES and ANDROIDS – Cybergy Picks
Cryptocurrency theft
This second script checks whether it is operating on a digital machine earlier than downloading an data stealer. As soon as every little thing is prepared, the hacker can entry the sufferer’s cryptocurrency. The scheme sends the sufferer’s funds to the hacker as a substitute of the meant recipient.
Different assault technique: electronic mail phishing
Proofpoint notes that dangerous actors additionally use one other technique known as “electronic mail lure” to put in malicious software program. Emails, often those who seem like work- or corporate-related, comprise an HTML file that resembles Microsoft Phrase. These emails immediate customers to put in the “Phrase On-line” extension to view the doc correctly.
Just like the strategy above, customers are prompted to open PowerShell and duplicate over the malicious code. Proofpoint says the fraudulent “marketing campaign” is widespread. Based on the agency, “The marketing campaign concerned greater than 100,000 messages and focused hundreds of organizations globally.”
HTML attachment containing directions on easy methods to copy and paste PowerShell that results in set up of malware (Proofpoint). (Kurt “Cyberguy” Knutson)
Don’t let your voicemail get bogged down with this quick tip
5 methods to guard your self from dangerous software program
Faux Chrome and Microsoft Phrase malware creates a way of urgency, inflicting customers to click on on hyperlinks and unknowingly compromise their gadgets. There are a number of steps you possibly can take to guard your self from such malware.
1) Have robust antivirus software program: One of the simplest ways to guard your self from clicking on malicious hyperlinks that set up malware that positive aspects entry to your private data is to put in antivirus safety on all of your gadgets. It may possibly additionally warn you to any phishing emails or ransomware scams. Get my picks for the best 2024 antivirus security winners for you Windows, Mac, Android and iOS devices.
2) Use a VPN: Think about using a VPN to keep away from being tracked and determine your potential location on web sites you go to. Many websites can learn your IP tackle and, relying on their privateness settings, show town you are from. A VPN will disguise your IP tackle to point out an alternate location. For the best VPN software, check out my expert review of the best VPNs for browsing the web privately Windows, Mac, Android and iOS devices.
3) Monitor your accounts: Recurrently evaluate your financial institution statements, bank card statements and different monetary accounts for any unauthorized exercise. Should you see any suspicious transactions, report them to your financial institution or bank card firm instantly.
4) Warn of Fraud: Contact one of many three main credit score reporting companies (Equifax, Experian or TransUnion) and request a fraud alert be positioned in your credit score file. It will make it tougher for identification thieves to open new accounts in your identify with out verification.
5) Allow two-factor authentication: allow Two-factor Authenticity Each time potential. It provides an additional layer of safety by requiring a second type of verification, like a code despatched to your cellphone, along with your password.
How to remove your personal data from the Internet
Kurt’s fundamental measures
Hackers have cleverly designed malware that tips you into putting in it in your gadgets. This malware particularly targets Home windows customers, and I’ve seen that Home windows gadgets appear to be extra prone to some of these assaults. Not too long ago, Microsoft admitted {that a} Wi-Fi driver flaw in Windows that allows hackers to hijack your PC Simply by being on the identical Wi-Fi community. It is very important watch out when shopping on-line or connecting to public Wi-Fi.
How do you confirm the authenticity of software program earlier than downloading and putting in it in your machine? Inform us by writing to us Cyberguy.com/Contact.
For extra of my tech ideas and safety alerts, subscribe to my free CyberGuy Report publication by visiting Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you want covered.
Comply with Kurt on his social channels
Solutions to probably the most steadily requested CyberGuy questions:
Copyright 2024 CyberGuy.com. all rights reserved.

